Check out how Moss takes care of the security of your servers
Moss sets up all your Ubuntu servers following industry’s best practices.
Firewall
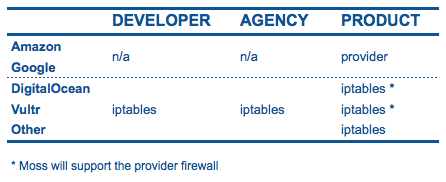
All servers connected to Moss are behind a firewall that it configures. Depending on your subscription and the cloud providers you use, Moss will set up the provider’s native firewall or equivalent iptables rules on each server.
Rules
Moss blocks all incoming traffic towards your server but the strictly needed for managing and running the services it hosts. In the following you can find the traffic allowed by default:
- ICMP (v4/v6) from any IP address
- SSH (tcp/22) from any IP address
- Server metrics (tcp/9100) from any IP address
- Local traffic (e.g. to allow your web application to connect to the database hosted on the same server via localhost)
You cannot delete the former firewall rules from Moss because they’re required to manage your servers. However, you can create additional rules and remove them afterwards if needed.
But Moss simplifies this task by adding the appropriate rules as you create websites and databases from Moss. In these cases, traffic towards the following services will be allowed:
- HTTP (tcp/80) from any IP address towards the web server
- HTTPS (tcp/443) from any IP address towards the web server
- MySQL (tcp/3306) from the web server towards the database server (in case the former connects with a remote database)
SSH
Moss configures your server so that you can always log into it via SSH or upload content onto it by means of SFTP. Moss doesn’t deploy the FTP service because of its lack of security, but you may use SFTP instead.
In order to prevent non-authorized accesses into the server, Moss implements the following additional configurations for SSH:
- Disables remote access as user root.
- By default, Moss disables password authentication and forces public key authentication instead. In this way Moss secures your server against brute-force attacks based on password dictionaries.
- But if you need to use passwords to access your servers via SSH or SFTP, you can do it without impacting their security. In this case, Moss only allows password auth for the specific server users that require it and automatically sets up fail2ban on your behalf. You can find more details in our blog.
Users
Moss automatically creates a user on your server.
- moss: Privileged user that’s allowed to run commands as root via sudo. The admin of the Moss account is the only one that can log into the server as user moss (unless they share their SSH private key, of course).
From Moss you can create additional non-privileged users. You usually employ such users to run their own website – you can isolate different websites on a same server in this way.
Both the admin and the teammates invited to the Moss account may log in the server as a non-privileged user (they just need to upload their SSH public key onto such user via Moss). In this way the developers of a team can do their job without messing with the system configuration, since they won’t have permission to make privileged changes.
Automatic security updates
Moss sets up unattended security updates on all servers it manages. This is the most convenient way to apply the latest patches for known vulnerabilities on your servers. After each update, Moss will send you a notification by email or the Slack channel of your choice to inform you about the changes that have taken place.
Moss only applies security updates automatically. Such updates come from official Ubuntu repositories and, in exceptional cases, from well maintained and supported PPAs.
Attack surface
Contrary to other products, Moss only installs the software that each server really needs. In this way, Moss minimizes the attack surface thus reducing the likelihood of compromising your server.
E.g. Moss won’t install Apache, Nginx or any other service which isn’t being used on a database server if that’s the only purpose of such machine. Hence, no web server vulnerability can be exploited to attack the database server.
Another example: if a web server only hosts static websites, Moss won’t install the PHP-FPM daemon. The software required for a PHP website will be installed as you create one on the server.
HTTPS
Moss sets up your websites to be served using the HTTPS secure protocol in a really simple way. You just have to choose one of these two options when creating your site:
- Provide your own TLS certificate. If you already own a valid certificate for your website, you just have to provide Moss with such certificate and the associated private key. Moss will configure your website to use this certificate.
- Choose the automatic certificate option for Let’s Encrypt. Moss will issue and renew free Let’s Encrypt certificates for your websites automatically.
Moss configures your website to redirect users that use HTTP towards HTTPS, thus preferring the secure version of the protocol.
Contact
If you find any security issue or have any doubt about how Moss manages the security of your servers, don’t hesitate to contact us 😄